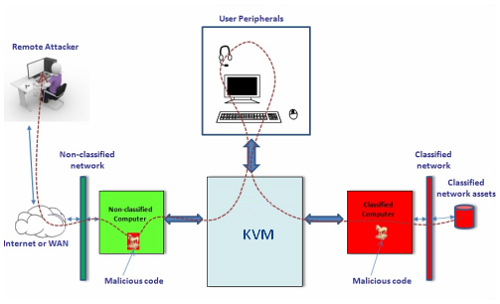
Network data leakage happens when the data residing on the secret network is passed through the Kernel-based Virtual Machine (KVM) and / or its peripherals to another (less secure) network where the attacker may receive it.
Attack process:
1. The remote attacker gains full / limited access to one connected computer (first computer).
2. Through that computer, the remote attacker finds a vulnerable connected KVM.
3. Through KVM, the remote attacker finds a vulnerable connected peripheral device having a mailbox.
4. Through other methods, the remote attacker injects a malicious code into the secret network connected to the same KVM through another computer.
5. The code on the secret network collects assets and loads them into the mailbox through the KVM.
6. When the KVM is switched to the first computer, it downloads the stored assets from the peripheral device.
7. Items 5 and 6 are repeated at any KVM switching cycle.
8. The remote attacker collects the assets and sends it to his remote location.
Rationale:
- T.INFECTED - At least one computer must be infected to initiate this attack.
- T.INVALIDPER - The use of invalid peripheral devices such as mass storage devices may support this attack by providing a large mailbox.
- T.DIRTRANSFER - The primary mode of attack is direct transfer of data through mailbox in peripherals.
- T.VALIDPER - All qualified peripheral tested had mailbox vulnerabilities.
Related Articles:
What is network code injection
What is audio leakage